1 FLag:
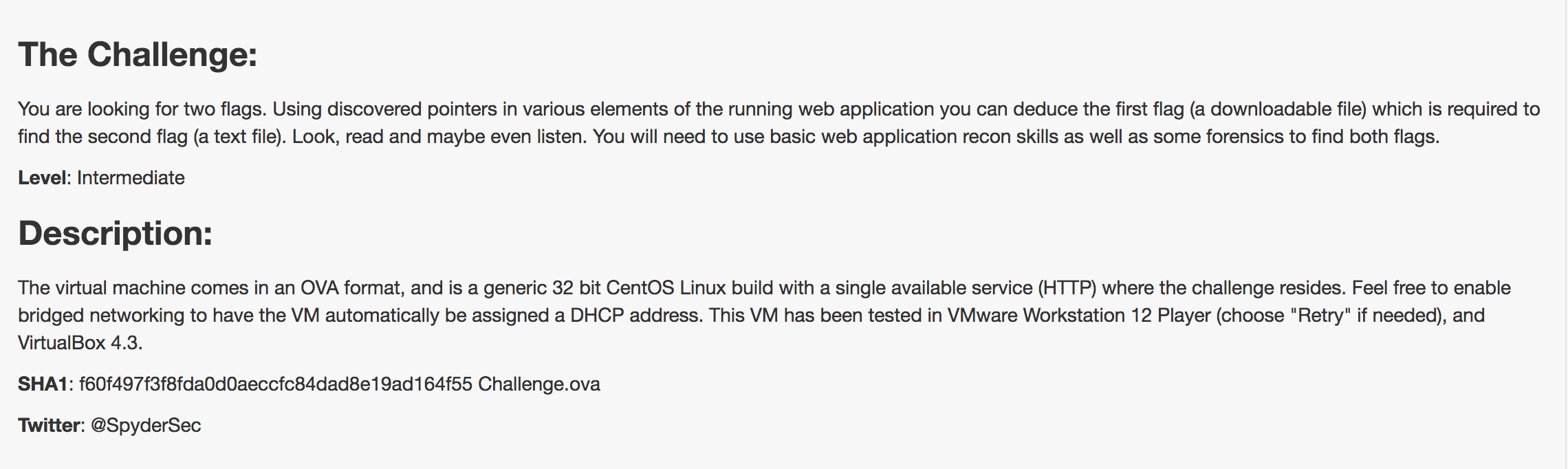
I used netdiscover to identify the IP of the machine.
192.168.0.27
Accessed the IP on the browser
I then used dirb directory burster to find available directories.
dirb http://192.168.0.27
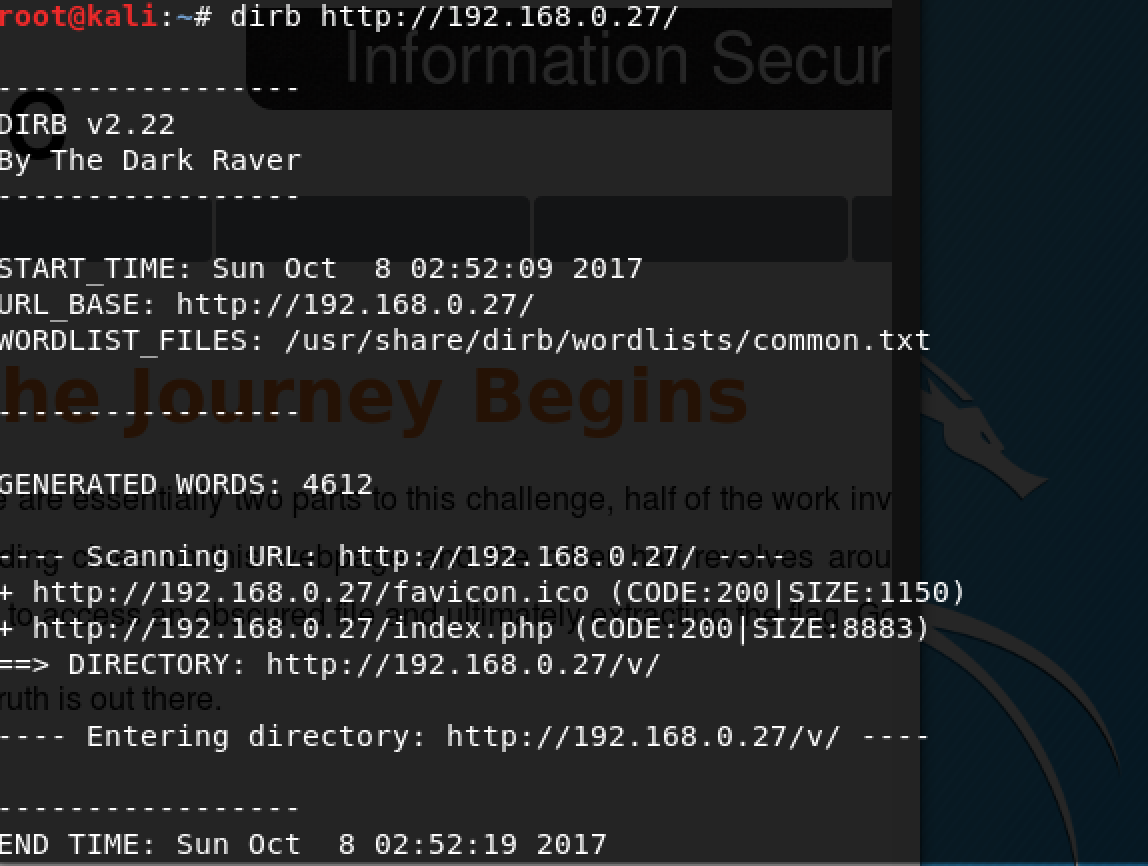
I found one directory, tried to access it but had no permissions.
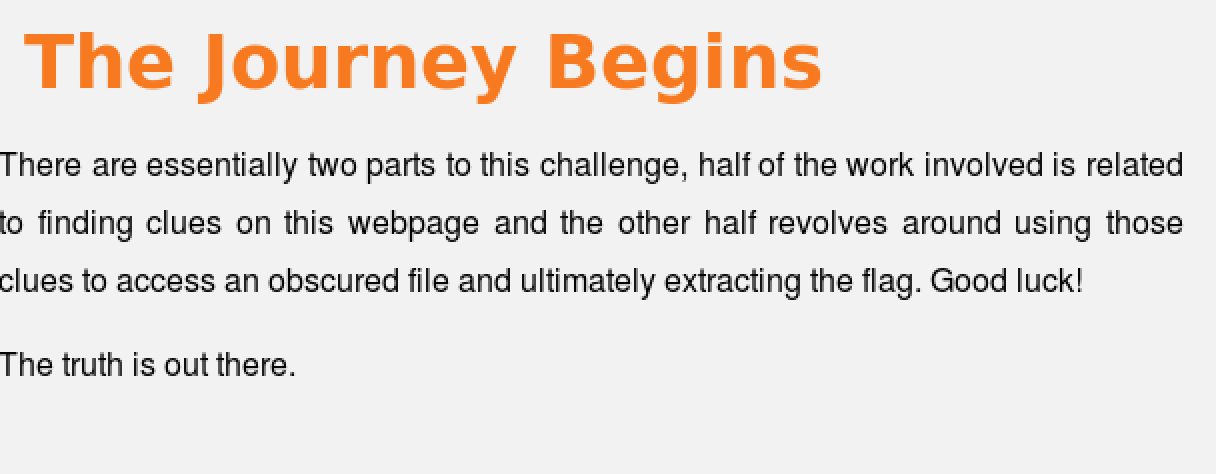
The application suggested that there are several clues on the page. Started by checking the page source. Had an interesting script. Didn’t know what to do with it.
Inspecting the page, under cookies there was another url, tried to access it, but still had no permissions.
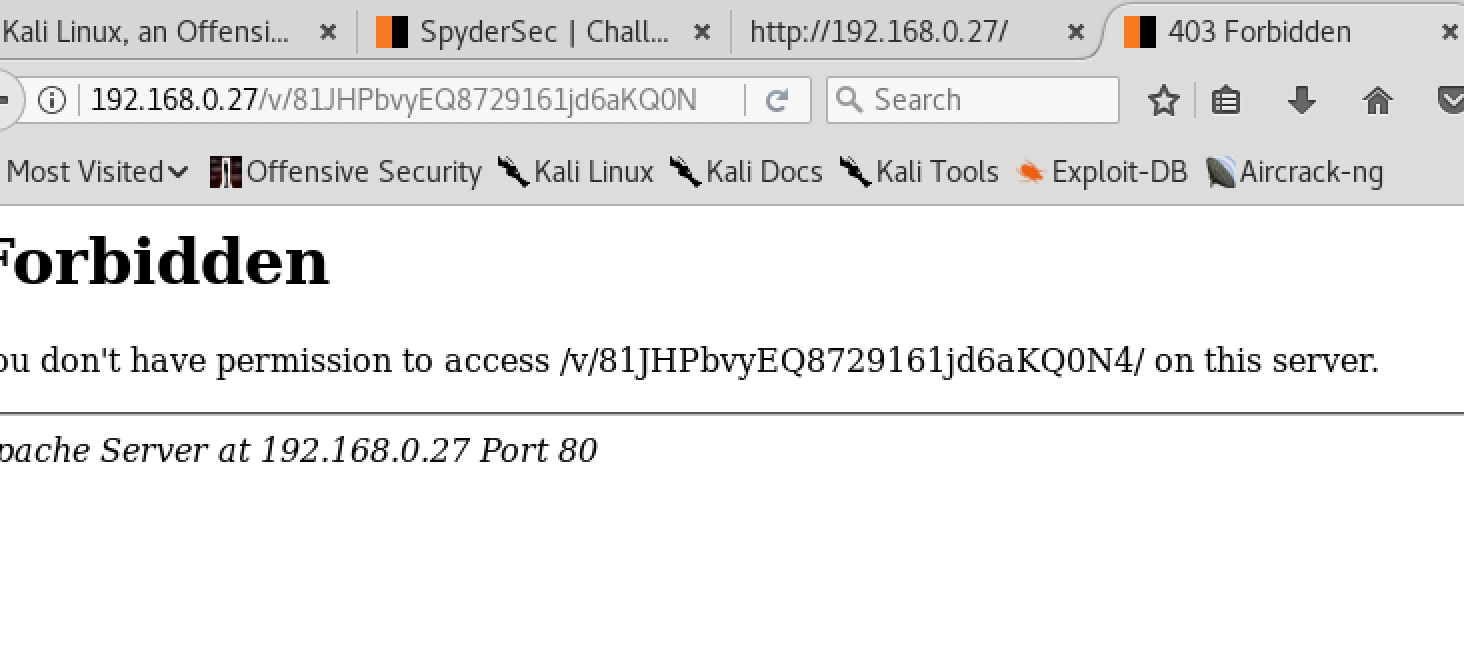
Took a step back to think of what i have so far, a script and a url that i cannot access. Decided to concentrate on the script as it might have a clue on how to access the url.
After a lot of googling on online tools that i can run my js script, i finally got http://matthewfl.com/unPacker.html. I used it to run the script. I got hexadecimal string. I removed the :.
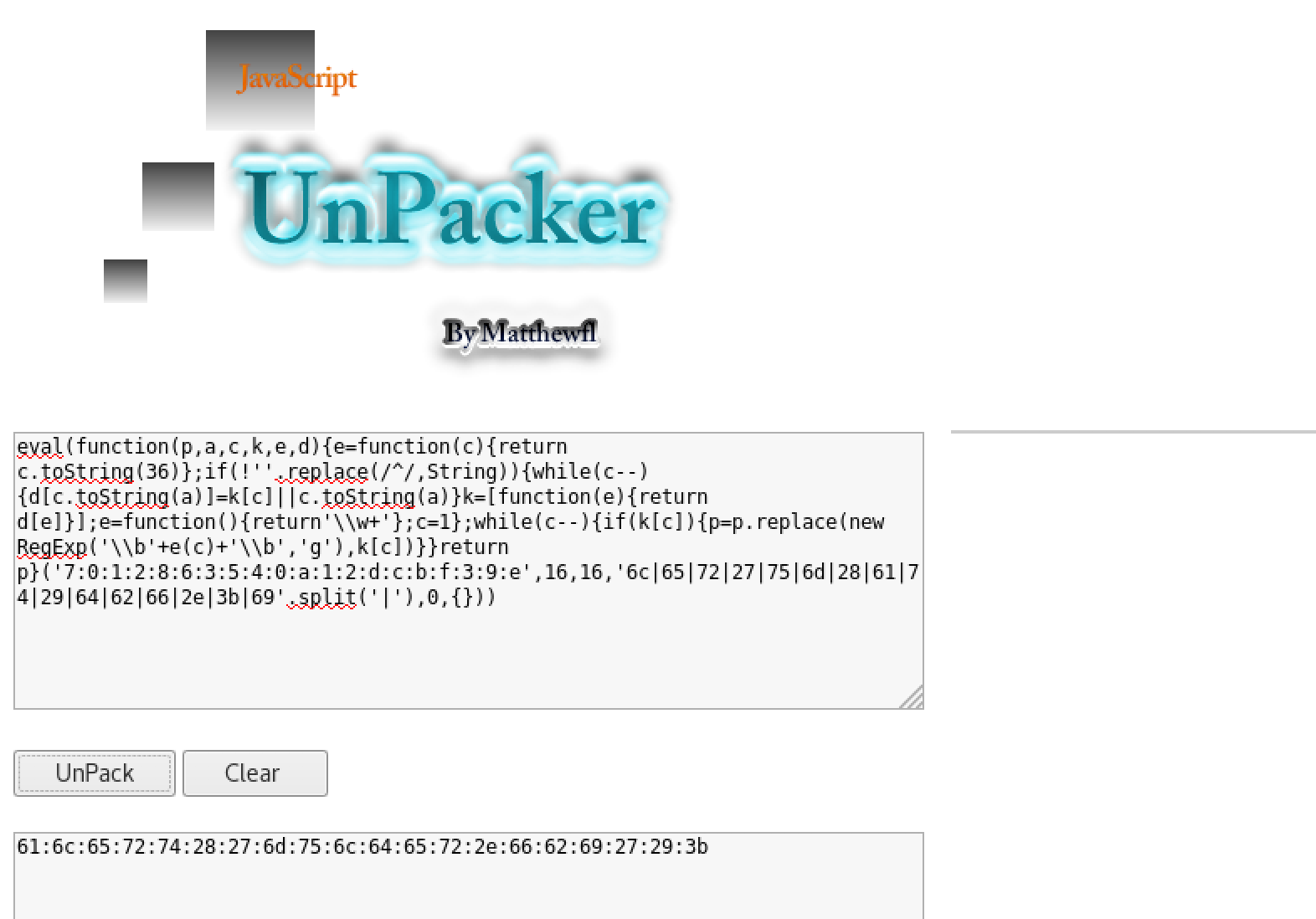
I tried to search for tools online to convert hexadecimal to text. I found http://www.convertstring.com/EncodeDecode/HexDecode which i used to convert to text. I later created my own python tool to convert this (I don’t want to search for it online everytime). You can find the code here, Converter
Here I will use the tool for all the conversion.
I copied the hex string to a file.
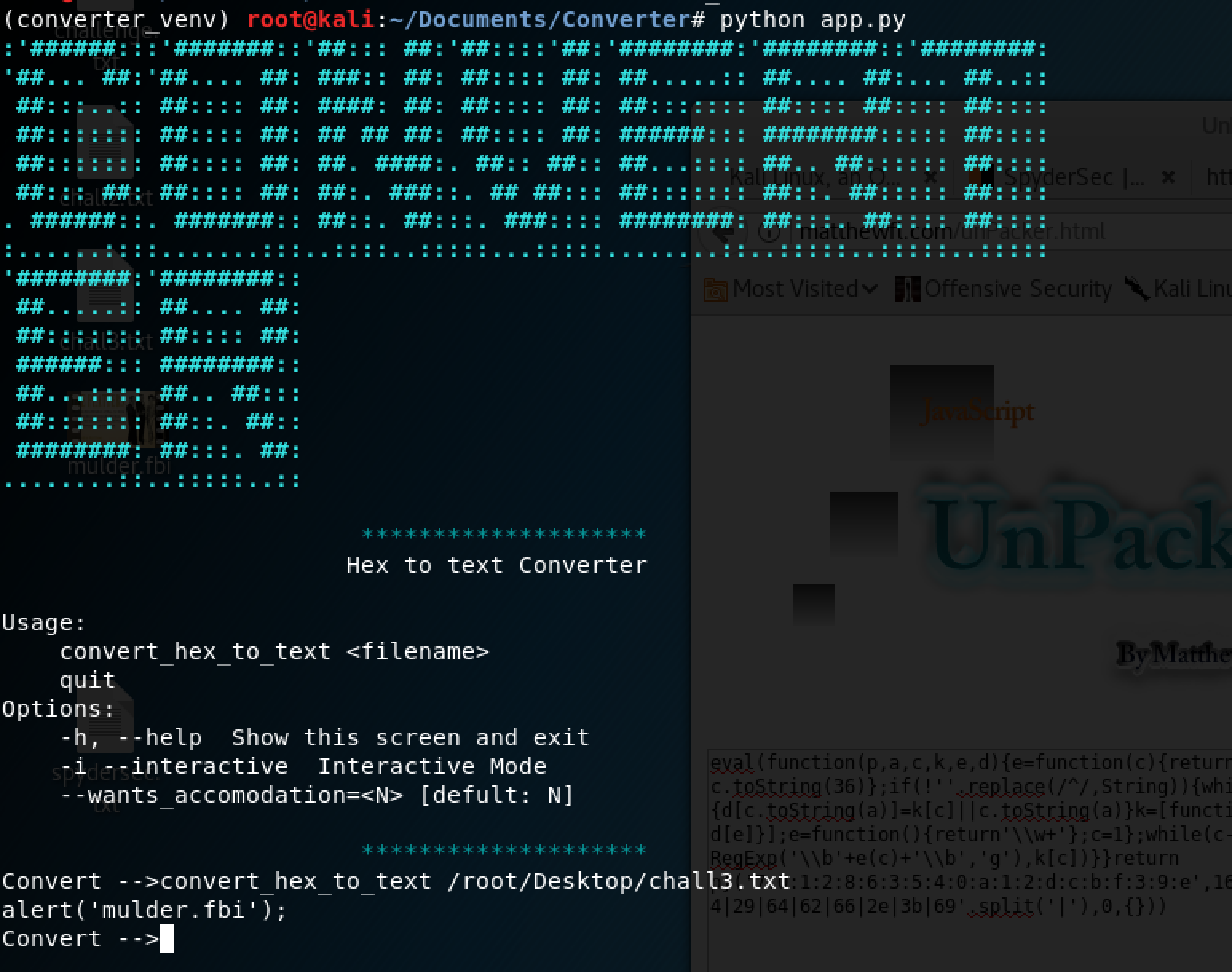
That looks like a file. Tried to access it with
http://192.168.0.2/mulder.fbi
http://192.168.0.2/v/mulder.fbi
And got request not found. Then i tried the previous url. I got a pop up to save a file. Looks like i have found my first flag.
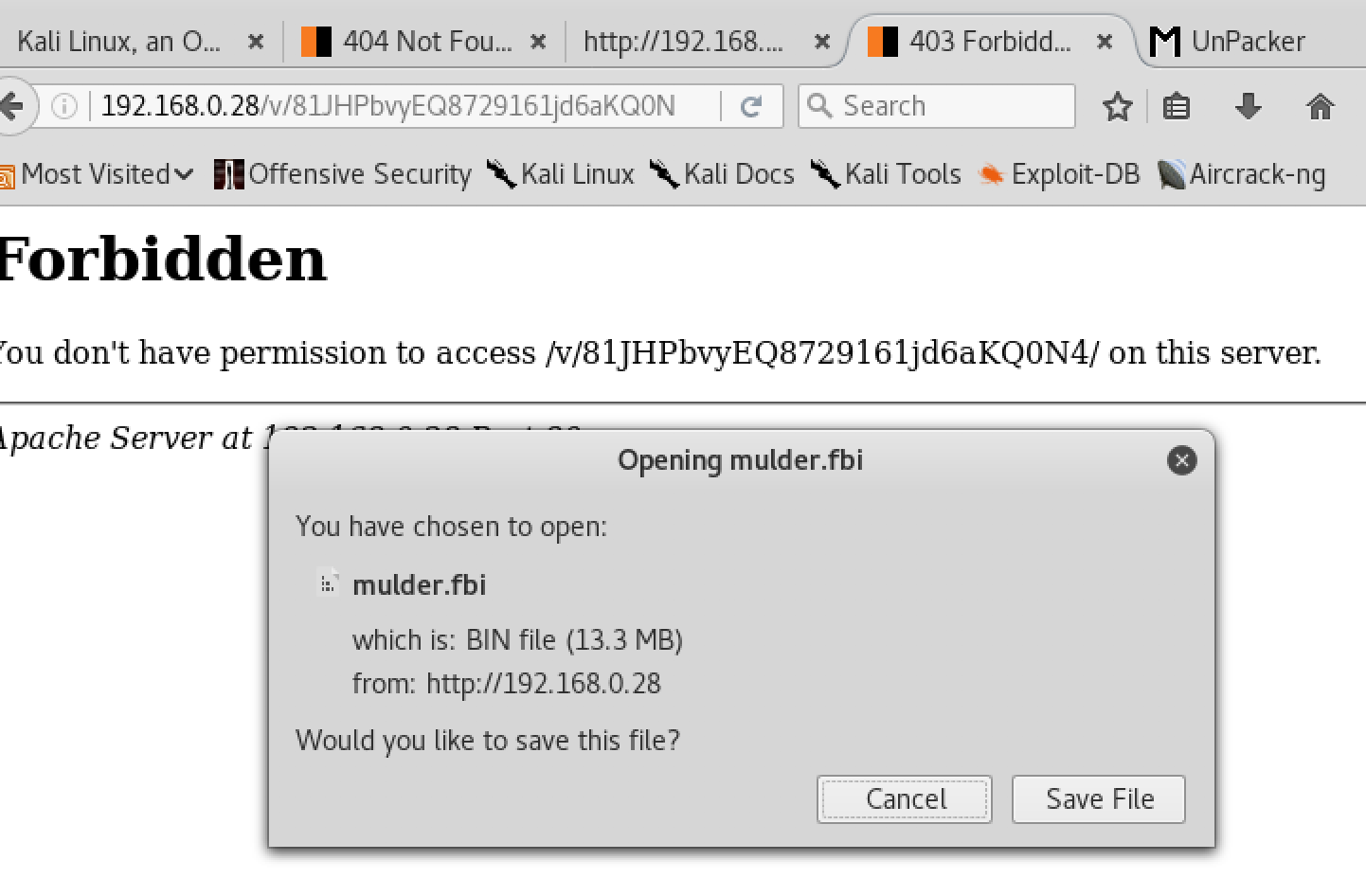
Saved the file.
2 FLag:
The file downloaded above was a video. Watched it with hope of finding a clue there. But there was none.
According to the challenge, the next flag is a text file. first flag (a downloadable file) which is required to find the second flag (a text file).
Somehow the video has the clue to the second flag.
I have heard that one can hide a message in another file as a secret method of communication. From what i understand, one can mount a file into another file with a key that will be used to decrypt the file. Which means only people who can rea/find the mounted file are those who have the keys.
I googled on wome of the tools that can be used to encrypt/decrypt data in a file. I found Veracrypt which was interesting.
I followed this guide to install it and learned the basics on how to use it.
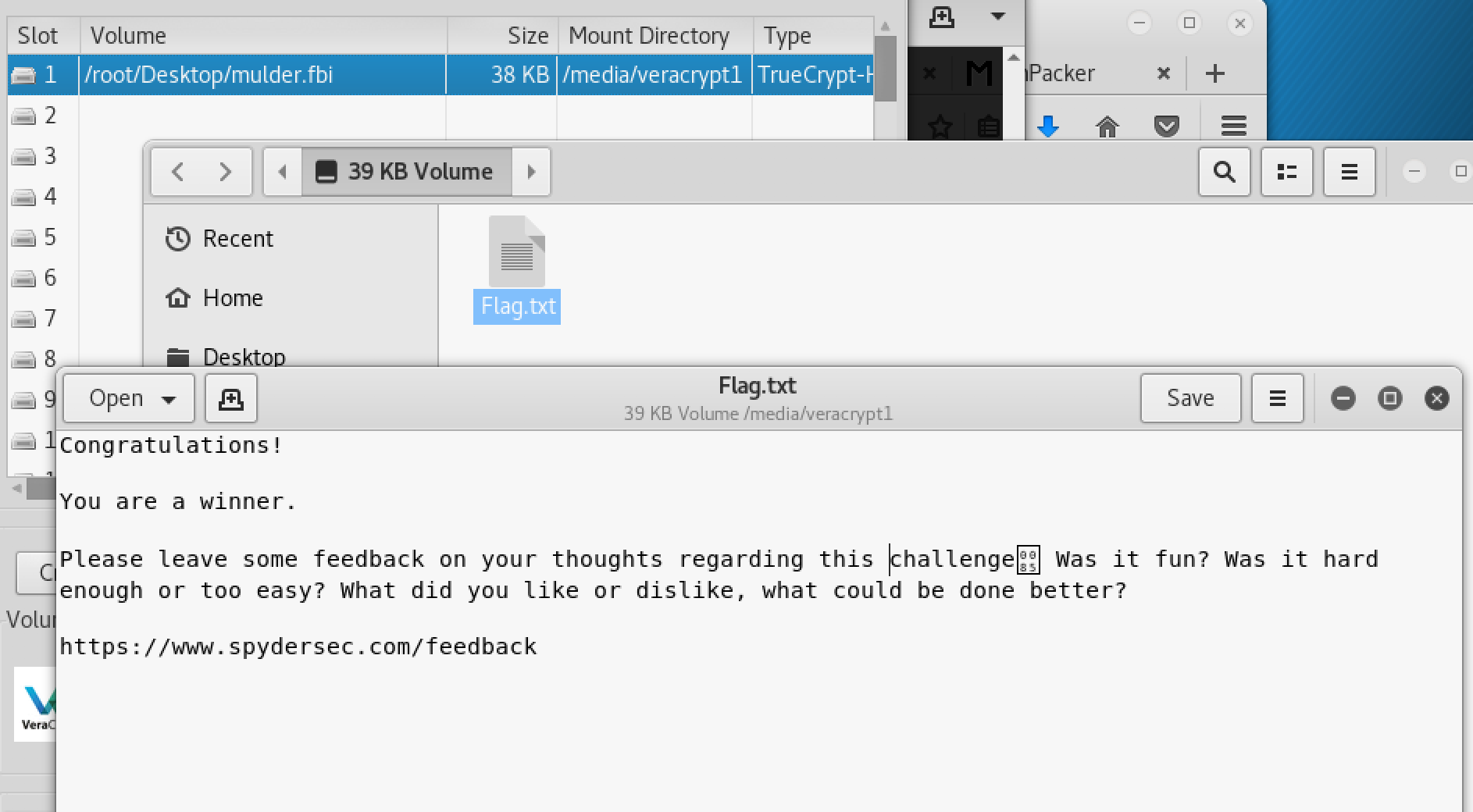
Trying to mount the file to a disk but it required a password which I don’t have at the moment.
Was back to page source to see if I missed the password there. There were two images there. I used exiftool that scan an image and extract all the info about the image. SpyderSecLogo.png had nothing unusual about the image content, but the Challenge.png had a hexadecimal on the comment field.
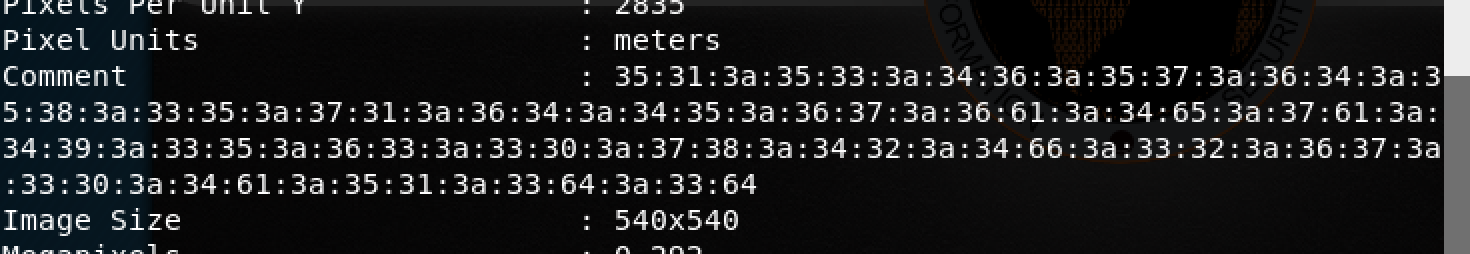
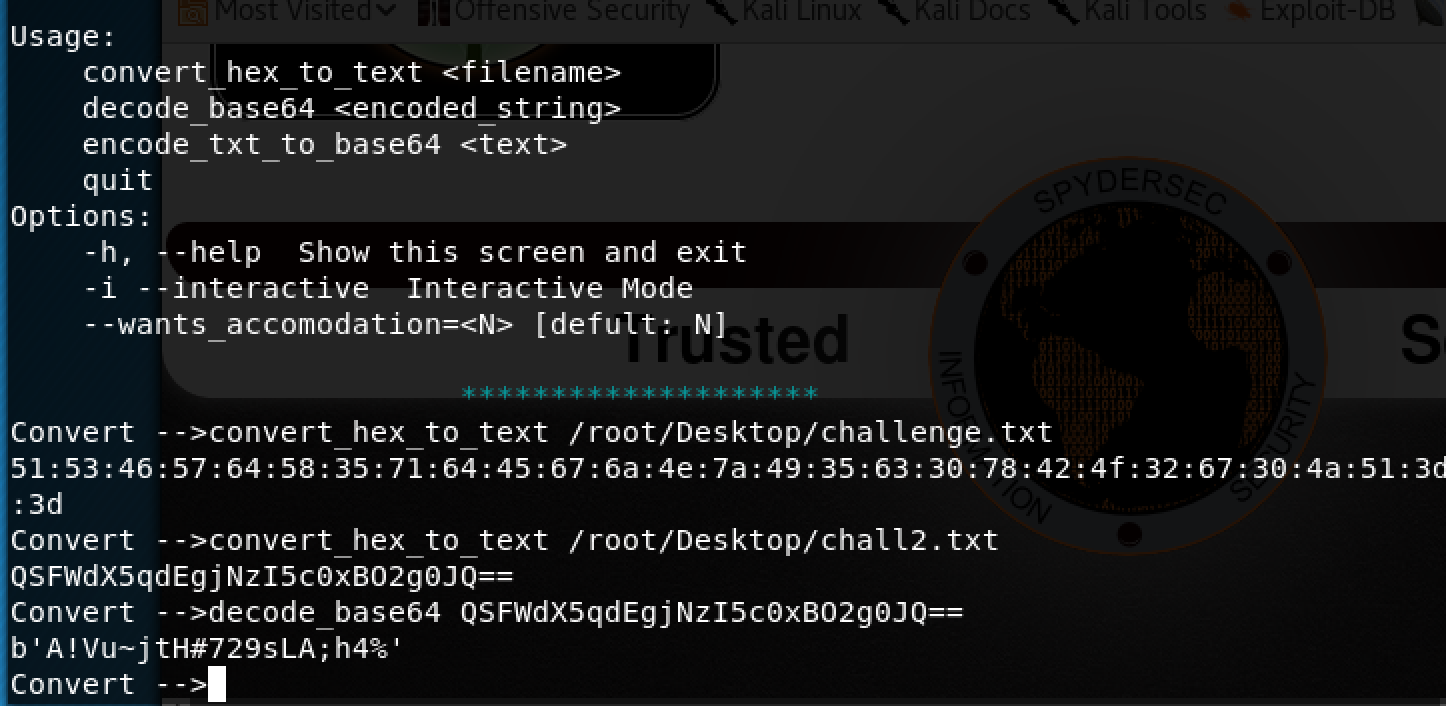
Copied the the hex to a file, and removed the :. Used my tool again to do the conversion. I got another hex, rerun the app and got a base64 encoded string.
I expanded my tool to decode and encode base64. I used it to decode and got a text string that looked like a password.
Back to veracrypt and used the text as the password.
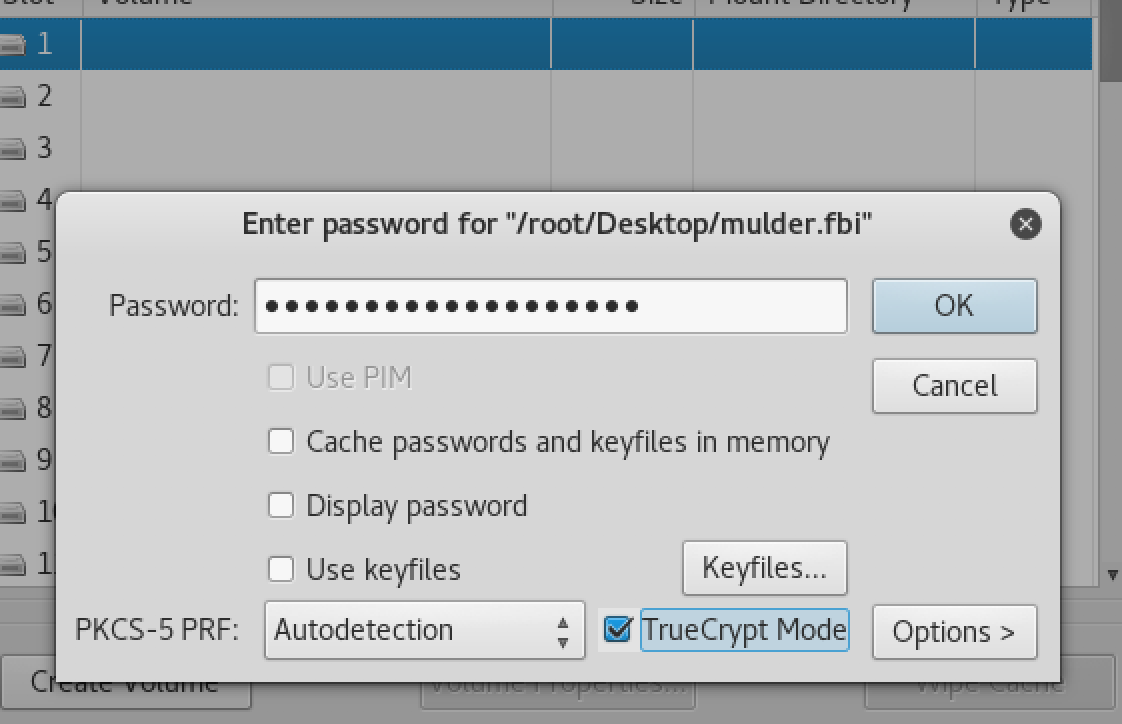
It mounted 38kb to the disk. Double clicked on the disk to open. It had a Flag.txt file. Opened the file and got a congratulations message. I had found the second flag.
Conclusion:
The CTF was awesome and challenging enough. I got to learn some of the tools that i added to my arsenal. I will be exploring more on how to hide messages in another file.