I recently dived into Denial of Service or well know as DOS course. In this blog I will be writing on what is DOS/DDOS?, how to perform DDOS? and how to prevent it?.
What is DOS?
As the name suggest, this is when an attacker make a service unavailable for legitimate users. You operate a delivery business that customers makes call to order their delivery, now the attacker makes the call and leave the line open and doesn’t make an order. The line stay opens for a while until you decide to hang up. The attacker make the call again, you hang up. The cycle continues keeping the line busy. Legitimate Customers trying to calls can’t go through because the line is currently busy. Below is an illustration of the same.
 Image Credit: resources.infosecinstitute.com
Image Credit: resources.infosecinstitute.com
What is DDOS?
This is a distributed dinial of service. As the name suggests, it is Distributed and more effective than DOS because the attack is coming from different sources. It can be coordinated and carried out by individuals that have the same motives or using botnets. Botnets is where we have attacker controlling other machine/PC called zombies(slaves) and issuing commands to them. Now instead of one attacker making call to your delivery business, you have multiple of them calling making it even harder for legitimate customers to reach you.
DDOS is Not really hacking as it does not involve getting access to any target. This does not make it less of a problem becaues a business can loose millions when hit by DDOS.
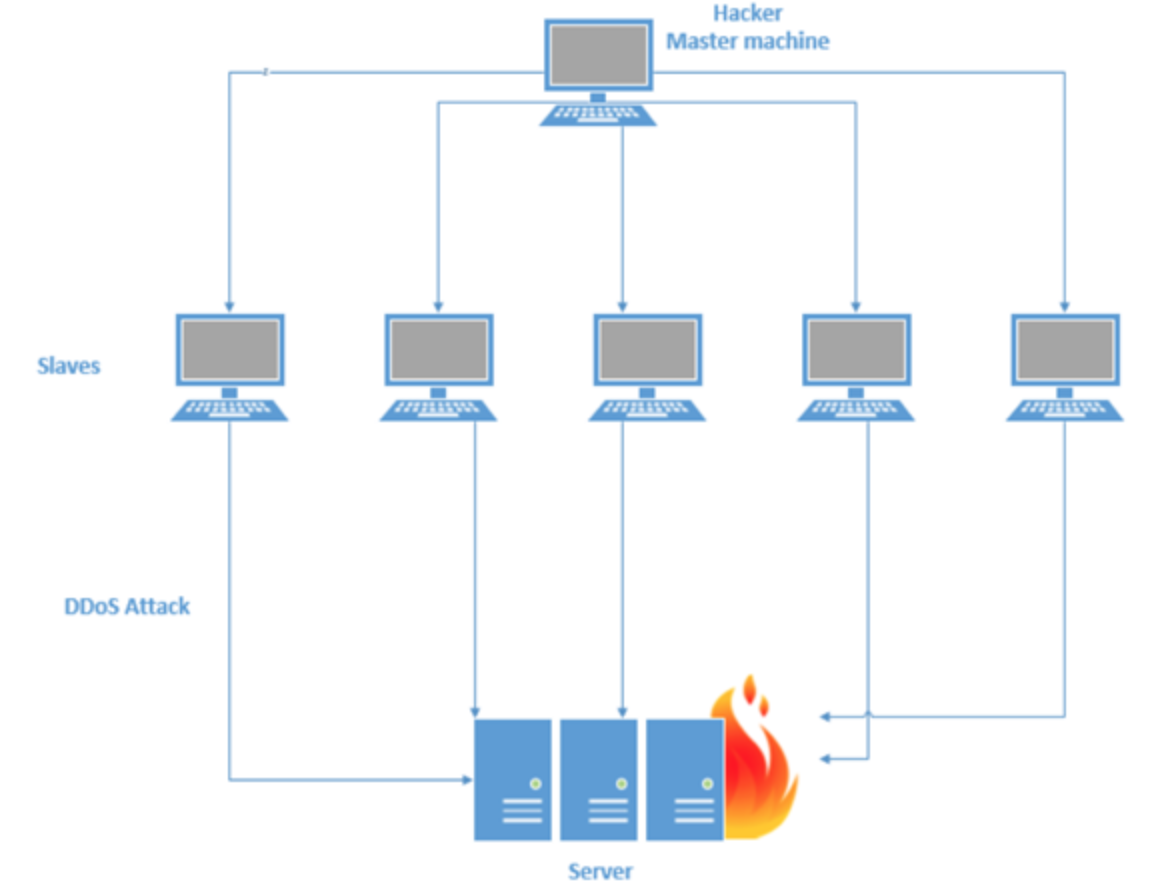 Image Credit: resources.infosecinstitute.com
Image Credit: resources.infosecinstitute.com
How to Perform DDOS?
It is very easy for anyone to perform this kind of attacks even without technical know how due to available tools or even services that can be acquired cheaply.
The attack can mainly target two layers of the OSI Model(Transport(4th layer which includes protocals like TCP, UDP and ICMP) and Application(7th layer which include HTTP)).
Techniques:
- Peer-to-peer attackes P2P networks are normally used used for file-sharing. The attacker uses the clients/users to redirect their connection to the target without their knowledge. This paper take a deeper look on P2P DDOS.
- HTTP flood attacks They are volumetric attacks that exploit legitimate HTTP GET or POST request to the server. The attack uses botnets to to effectively exhaust the resources of the target. Requests that requires more processing power on the server side are targeted to achive exhaustion of the server much quicker. Simply put, so many request are sent to the server at the same time that it cannot handle the request anymore even for legitimate users.
- Slowloris As the name suggests, it is slow and low in bandwidth. It works by sending partial request to the server and keeping the connection open. It keep on continuously sending incomplete HTTP requests and server keeps on opening connection awaiting for the request to be completed. Eventually the server connections pool is full and can’t accept additional request even from legitimate users.
- Permanent DOS and Phlashing - This is replacing the firmware of the device with either one that is vulnerable to make the device unusable. It is commonly known as bricking the device.
Tools:
Below are some of the tools that you can use to automate DDOS attacks. They are so easy to use, even the person with no technical knowledge can use them.
- LOIC
- DosHTTP
- Sprut
Most of these tools are marketed as stressers tools as there is a question about their legitimacy. There are services that do offer legitimate stress tests, loader.io is one of them.
How to Defend Against DDOS Attack?
Being prepared to deal with a DDOS attack is very important for your business. Since you cannot be sure on which DDOS attack will be directed to you, it is better to have a multi-faceted implementation that defend you from most if not all kind of DDOS attacks. Below I outline some of the options you can implement.
Absord attacks This is when your infrastructure is able to absorb the attacks without disrupting your normal users experience. The attack does not take your service down. Capacity > Attacks You have the ability to scale the infrustructure easily. With this age of cloud, scaling your infratructure resources can be done easily. This is not all you need as an attack can be massive but it does give you time to explore the attack and mitigate the impact. It is also expensive to maintain and you will need to identify malicious traffic and block them.
Traffic Reputation It is important to understand how your normal traffic look like, where does it come from and so on. This way, you can easily identify when traffic that you not used to hit your server. You can use traffic reputation to block traffic you think is malicious depending on the scale of deviation from your normal traffic pattern you consider dangerous.
Network level defense Blocking all malicious traffic at network infrastructure level by disabling all unused ports, blocking unnecessary protocols and filtering ingress traffic. We can also implement blackholing - a technique that directs the traffic somewhere else without sending a response back. From there, we can analyze the requests to understand the attack better. A major limitation to this defense is that it only works if network is not saturated with data and have enough capacity.
Application Level Defenses Sometimes malicious traffic can pass through the network defenses as it might be targeting HTTP. This is where devices like WAF(Web Application Firewall) come in handy. They have all the rules that to inspect the HTTP request to determine malicious traffic and block them. It is very important that you able to inspect HTTPS traffic as well as the attack can be over HTTPS.
Another defense here is minimizing the attack surface area. What this means is that, any resource that doesn’t need to be public, keep it in the private network of your infrustructure.
Sandboxing your application features can also help and minimize the impact of the attack. Attack on a certain feature of the application will only affect the server that serves that feature leaving all the other features functional to the real users.
AnyCast Implementation - a webserver has different nodes that serves the clients from all over the world improving on the performance and also mitigating on the DOS attacks. Attack from one region will only affect nodes in that region alone. Even if the attack is distributed, the server will not be hit by all the traffic but the nodes will be. We can then implement all the above defenses on node level which improves defense against DDOS.
Preparing For DDOS Resilience
Being prepared is very important for your business. Here is a checklist to ensure you ready.
- Have you implemented DDOS strategy?
- HAve you tested your strategy?
- Do you have a crisis management plan?
- What will a succsseful DDOS cost you?
Thanks to Troy Hunt course on pluralsight.
The material shared here is solely meant for learning purposes and the writer does don’t bare any responsibilty if used otherwise.